Entra Conditional Access
Cloud Security Guard
Secure your resources cloud with conditional access
Traditional network boundaries are dissolving at Cloud. What remains is a multitude of endpoints accessing sensitive corporate data from anywhere. This gives companies more opportunities to increase efficiency, but these access options also present an equally significant risk. This enables comprehensive and powerful monitoring that not only verifies identities, but also records and controls access to company data from different endpoints at Cloud.
Conditional access is a native part of Entra ID / Azure AD and . Office 365 . It helps enforce corporate policies on all endpoints, whether a private tablet or a corporate desktop.
Overview
Brief overview of the conditional access
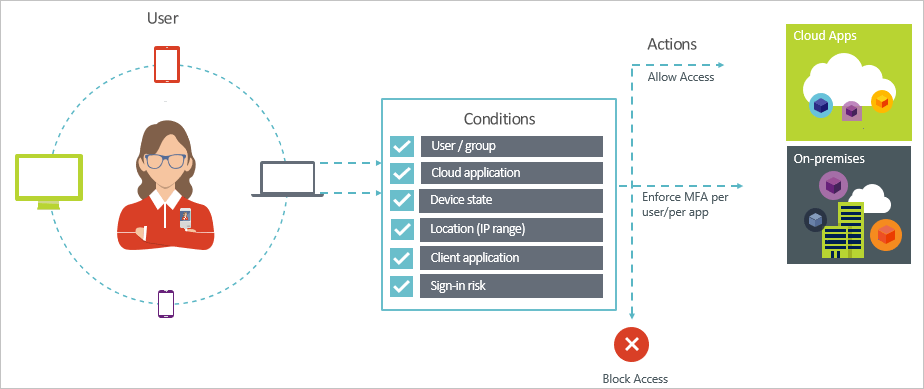
Two birds with one stone
In fact
Endpoint Security
Let's go further together!
If you have a question or a suggestion, we are at your disposal to answer it by email or by phone.
Articles on Conditional Access
Guide to Azure AD Conditional Access
Conditional Access is one of Microsoft's most powerful security features and the core engine of their Zero Trust architecture. In our opinion it should be the foundation of any Zero Trust strategy for organizations based on cloud. However, if you don't understand how conditional access works, it could bring you a [...]
Manage authentication sessions in Conditional Access AAD

Authentication session management capabilities allow you to configure how often your users need to provide login credentials and whether they need to provide credentials after closing and reopening browsers, giving you fine-grained controls that can provide more security and flexibility in your business.
Manage your Teams Rooms Systems with Intune
This article is intended to answer some common questions and provide general advice but does not replace the full recommendations of experts Lambert Consulting. The Teams Rooms Systems (TRS) or Skype Room Systems (SRS) can be registered and managed by Intune to provide many of the device management features and [...]
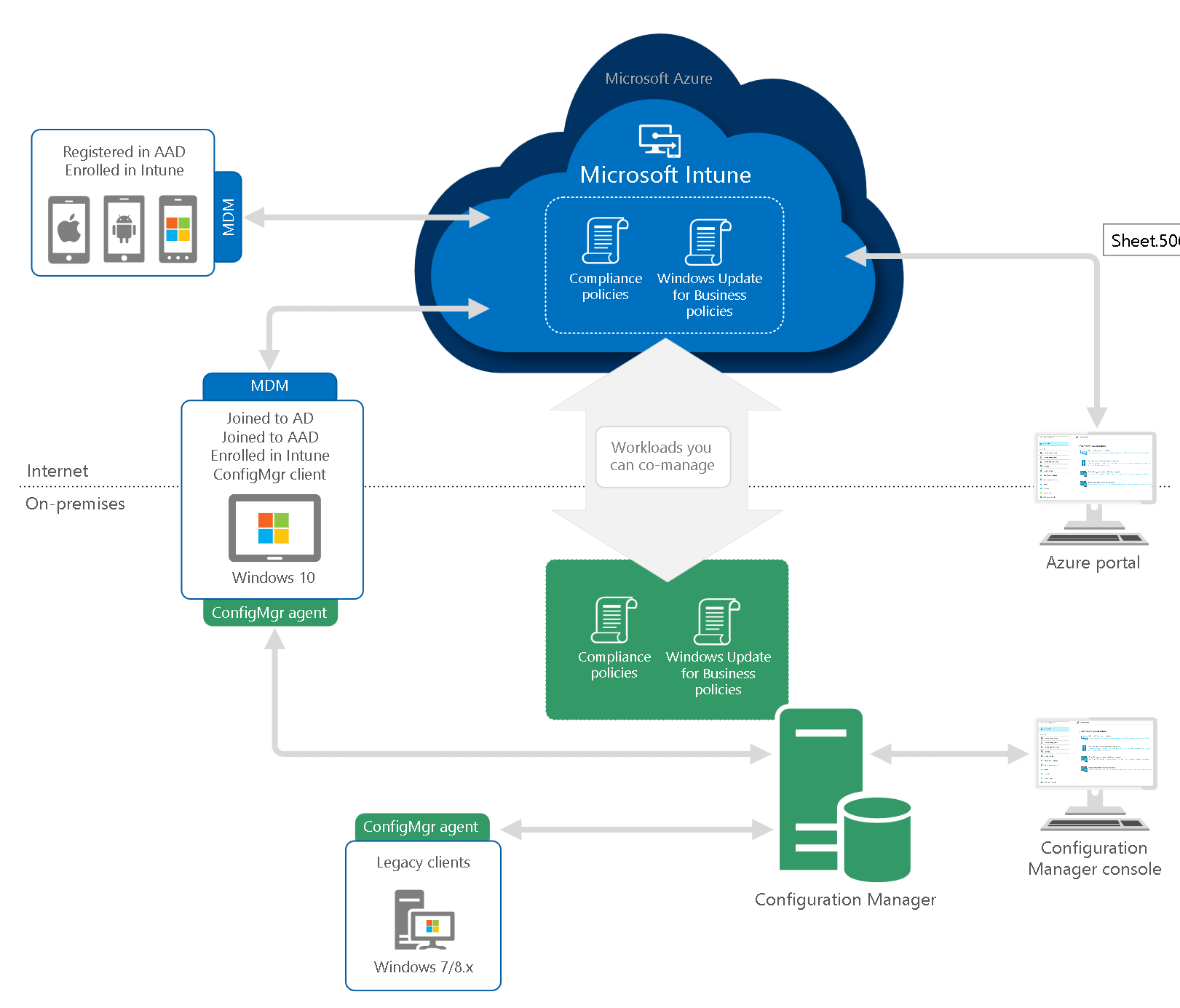
Deployment options for Co-Management with your MDM
As mentioned in our article, "co-management" or co-management is the first fundamental step on the road to modern management to be able to use existing Windows devices and configuration "as is", while adding a modern management tool. After that, you can move on to Modern Management, as the move to the world of [...]
